Completing the LASCON 2018 Badge Game
The LASCON Badge Game was back in 2018 and the feedback I received was that it was the best one so far. It started out with the following QR code on the back of the badge:

Following that QR code took you to the URL https://pastebin.com/J61kDSe2. Viewing that URL gives you the following:
V2VsY29tZSB0byB0aGUgTEFTQ09OIDIwMTggYmFkZ2UgZ2FtZSF= V2VsY29tZSB0byB0aGUgTEFTQ09OIDIwMTggYmFkZ2UgZ2FtZSE= V2VsY29tZSB0byB0aGUgTEFTQ09OIDIwMTggYmFkZ2UgZ2FtZSH= V2VsY29tZSB0byB0aGUgTEFTQ09OIDIwMTggYmFkZ2UgZ2FtZSG= V2VsY29tZSB0byB0aGUgTEFTQ09OIDIwMTggYmFkZ2UgZ2FtZSF= V2VsY29tZSB0byB0aGUgTEFTQ09OIDIwMTggYmFkZ2UgZ2FtZSF= V2VsY29tZSB0byB0aGUgTEFTQ09OIDIwMTggYmFkZ2UgZ2FtZSF= V2VsY29tZSB0byB0aGUgTEFTQ09OIDIwMTggYmFkZ2UgZ2FtZSE= V2VsY29tZSB0byB0aGUgTEFTQ09OIDIwMTggYmFkZ2UgZ2FtZSF= V2VsY29tZSB0byB0aGUgTEFTQ09OIDIwMTggYmFkZ2UgZ2FtZSF= V2VsY29tZSB0byB0aGUgTEFTQ09OIDIwMTggYmFkZ2UgZ2FtZSE= V2VsY29tZSB0byB0aGUgTEFTQ09OIDIwMTggYmFkZ2UgZ2FtZSF= V2VsY29tZSB0byB0aGUgTEFTQ09OIDIwMTggYmFkZ2UgZ2FtZSF= V2VsY29tZSB0byB0aGUgTEFTQ09OIDIwMTggYmFkZ2UgZ2FtZSH= V2VsY29tZSB0byB0aGUgTEFTQ09OIDIwMTggYmFkZ2UgZ2FtZSF= V2VsY29tZSB0byB0aGUgTEFTQ09OIDIwMTggYmFkZ2UgZ2FtZSF= V2VsY29tZSB0byB0aGUgTEFTQ09OIDIwMTggYmFkZ2UgZ2FtZSF= V2VsY29tZSB0byB0aGUgTEFTQ09OIDIwMTggYmFkZ2UgZ2FtZSE= V2VsY29tZSB0byB0aGUgTEFTQ09OIDIwMTggYmFkZ2UgZ2FtZSH= V2VsY29tZSB0byB0aGUgTEFTQ09OIDIwMTggYmFkZ2UgZ2FtZSF= V2VsY29tZSB0byB0aGUgTEFTQ09OIDIwMTggYmFkZ2UgZ2FtZSF= V2VsY29tZSB0byB0aGUgTEFTQ09OIDIwMTggYmFkZ2UgZ2FtZSG= V2VsY29tZSB0byB0aGUgTEFTQ09OIDIwMTggYmFkZ2UgZ2FtZSG= V2VsY29tZSB0byB0aGUgTEFTQ09OIDIwMTggYmFkZ2UgZ2FtZSG= V2VsY29tZSB0byB0aGUgTEFTQ09OIDIwMTggYmFkZ2UgZ2FtZSF= V2VsY29tZSB0byB0aGUgTEFTQ09OIDIwMTggYmFkZ2UgZ2FtZSE= V2VsY29tZSB0byB0aGUgTEFTQ09OIDIwMTggYmFkZ2UgZ2FtZSG= V2VsY29tZSB0byB0aGUgTEFTQ09OIDIwMTggYmFkZ2UgZ2FtZSF= V2VsY29tZSB0byB0aGUgTEFTQ09OIDIwMTggYmFkZ2UgZ2FtZSE= V2VsY29tZSB0byB0aGUgTEFTQ09OIDIwMTggYmFkZ2UgZ2FtZSH= V2VsY29tZSB0byB0aGUgTEFTQ09OIDIwMTggYmFkZ2UgZ2FtZSE= V2VsY29tZSB0byB0aGUgTEFTQ09OIDIwMTggYmFkZ2UgZ2FtZSG= V2VsY29tZSB0byB0aGUgTEFTQ09OIDIwMTggYmFkZ2UgZ2FtZSF= V2VsY29tZSB0byB0aGUgTEFTQ09OIDIwMTggYmFkZ2UgZ2FtZSE= V2VsY29tZSB0byB0aGUgTEFTQ09OIDIwMTggYmFkZ2UgZ2FtZSH= V2VsY29tZSB0byB0aGUgTEFTQ09OIDIwMTggYmFkZ2UgZ2FtZSE= V2VsY29tZSB0byB0aGUgTEFTQ09OIDIwMTggYmFkZ2UgZ2FtZSF= V2VsY29tZSB0byB0aGUgTEFTQ09OIDIwMTggYmFkZ2UgZ2FtZSG= V2VsY29tZSB0byB0aGUgTEFTQ09OIDIwMTggYmFkZ2UgZ2FtZSG= V2VsY29tZSB0byB0aGUgTEFTQ09OIDIwMTggYmFkZ2UgZ2FtZSG= V2VsY29tZSB0byB0aGUgTEFTQ09OIDIwMTggYmFkZ2UgZ2FtZSF= V2VsY29tZSB0byB0aGUgTEFTQ09OIDIwMTggYmFkZ2UgZ2FtZSG= V2VsY29tZSB0byB0aGUgTEFTQ09OIDIwMTggYmFkZ2UgZ2FtZSF= V2VsY29tZSB0byB0aGUgTEFTQ09OIDIwMTggYmFkZ2UgZ2FtZSH= V2VsY29tZSB0byB0aGUgTEFTQ09OIDIwMTggYmFkZ2UgZ2FtZSE= V2VsY29tZSB0byB0aGUgTEFTQ09OIDIwMTggYmFkZ2UgZ2FtZSH= V2VsY29tZSB0byB0aGUgTEFTQ09OIDIwMTggYmFkZ2UgZ2FtZSF= V2VsY29tZSB0byB0aGUgTEFTQ09OIDIwMTggYmFkZ2UgZ2FtZSF= V2VsY29tZSB0byB0aGUgTEFTQ09OIDIwMTggYmFkZ2UgZ2FtZSF= V2VsY29tZSB0byB0aGUgTEFTQ09OIDIwMTggYmFkZ2UgZ2FtZSE= V2VsY29tZSB0byB0aGUgTEFTQ09OIDIwMTggYmFkZ2UgZ2FtZSH= V2VsY29tZSB0byB0aGUgTEFTQ09OIDIwMTggYmFkZ2UgZ2FtZSE= V2VsY29tZSB0byB0aGUgTEFTQ09OIDIwMTggYmFkZ2UgZ2FtZSF= V2VsY29tZSB0byB0aGUgTEFTQ09OIDIwMTggYmFkZ2UgZ2FtZSG= V2VsY29tZSB0byB0aGUgTEFTQ09OIDIwMTggYmFkZ2UgZ2FtZSG= V2VsY29tZSB0byB0aGUgTEFTQ09OIDIwMTggYmFkZ2UgZ2FtZSG= V2VsY29tZSB0byB0aGUgTEFTQ09OIDIwMTggYmFkZ2UgZ2FtZSF= V2VsY29tZSB0byB0aGUgTEFTQ09OIDIwMTggYmFkZ2UgZ2FtZSE= V2VsY29tZSB0byB0aGUgTEFTQ09OIDIwMTggYmFkZ2UgZ2FtZSF= V2VsY29tZSB0byB0aGUgTEFTQ09OIDIwMTggYmFkZ2UgZ2FtZSF= V2VsY29tZSB0byB0aGUgTEFTQ09OIDIwMTggYmFkZ2UgZ2FtZSF= V2VsY29tZSB0byB0aGUgTEFTQ09OIDIwMTggYmFkZ2UgZ2FtZSH= V2VsY29tZSB0byB0aGUgTEFTQ09OIDIwMTggYmFkZ2UgZ2FtZSG= V2VsY29tZSB0byB0aGUgTEFTQ09OIDIwMTggYmFkZ2UgZ2FtZSF= V2VsY29tZSB0byB0aGUgTEFTQ09OIDIwMTggYmFkZ2UgZ2FtZSF= V2VsY29tZSB0byB0aGUgTEFTQ09OIDIwMTggYmFkZ2UgZ2FtZSE= V2VsY29tZSB0byB0aGUgTEFTQ09OIDIwMTggYmFkZ2UgZ2FtZSH= V2VsY29tZSB0byB0aGUgTEFTQ09OIDIwMTggYmFkZ2UgZ2FtZSF= V2VsY29tZSB0byB0aGUgTEFTQ09OIDIwMTggYmFkZ2UgZ2FtZSF= V2VsY29tZSB0byB0aGUgTEFTQ09OIDIwMTggYmFkZ2UgZ2FtZSE= V2VsY29tZSB0byB0aGUgTEFTQ09OIDIwMTggYmFkZ2UgZ2FtZSE= V2VsY29tZSB0byB0aGUgTEFTQ09OIDIwMTggYmFkZ2UgZ2FtZSF= V2VsY29tZSB0byB0aGUgTEFTQ09OIDIwMTggYmFkZ2UgZ2FtZSE= V2VsY29tZSB0byB0aGUgTEFTQ09OIDIwMTggYmFkZ2UgZ2FtZSH= V2VsY29tZSB0byB0aGUgTEFTQ09OIDIwMTggYmFkZ2UgZ2FtZSH= V2VsY29tZSB0byB0aGUgTEFTQ09OIDIwMTggYmFkZ2UgZ2FtZSF= V2VsY29tZSB0byB0aGUgTEFTQ09OIDIwMTggYmFkZ2UgZ2FtZSE= V2VsY29tZSB0byB0aGUgTEFTQ09OIDIwMTggYmFkZ2UgZ2FtZSH= V2VsY29tZSB0byB0aGUgTEFTQ09OIDIwMTggYmFkZ2UgZ2FtZSH= V2VsY29tZSB0byB0aGUgTEFTQ09OIDIwMTggYmFkZ2UgZ2FtZSF=
These are clearly BASE64 encoded strings and if you do a BASE64 decode on any of them, you get text that reads “Welcome to the LASCON 2018 badge game!”.
Each of the BASE64 encoded strings represents a 00, 01, 10, or 11 value, which is represented by changing the last character of the BASE64 encoded string. To learn more about this form of steganography, take a look at this CTF writeup.
Translating each of the strings in pastebin into a 00, 01, 10, or 11 value will give you a binary string value of:

Converting that string to ASCII text, you get:
NTQuMjI2Ljg5LjEyMA==
This looks like another BASE64 encoded string and decoding it gives you 54.226.89.120, which is obviously an IP address.
If you’re following along with me this far, you’ve gotten as far as you can go as the server hosting the badge game is no longer online. However, when you went to 54.226.89.120, you saw a file named lasconbadgegame.pcapng.zip. This was a packet capture file with a bunch of random web surfing contained in it, but if you isolated the requests to the 54.226.89.120 IP address, you would see a request for port 7777, port 8080, port 9797, and finally port 31337. The system was running a port knocking application that would open a hole in the firewall to port 31337 for any IP that hit the other three ports first, in the proper order.
Under http://54.226.89.120:31337 there was a submit.php page with a login prompt, a winners.php page that shows a list of who has won the game so far and when, an encrypted submission_password.zip file, and a rockyou-20.txt file which contained the RockYou word list.
You needed to take the rockyou-20.txt file and brute force it against the submission_password.zip file. Here’s what it looked like when I ran it using the fcrackzip application:
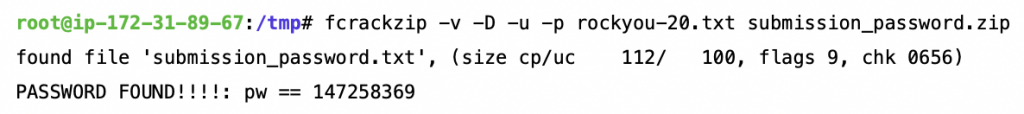
Using the found password of “147258369” to decompress the submission_password.zip file, the resulting submission_password.txt file contained the following text:

Looking at the submit.php page source code, there’s a comment line that reads:

Simply log in to http://54.226.89.120:31337/submit.php with the username “lascon” and password “P6KKWZQeKvMvTvBGNsvX” and submit your personal information to win. That was it! Another awesome LASCON Badge Game in the books and most I spoke with said it was the best one yet. Winners received this awesome LASCON 2019 Badge Game Challenge Coin…