Completing the LASCON 2017 Badge Game
For those who don’t know, every year I put together a game that starts on the back of the LASCON badge. It’s typically some combination of crypto challenges alongside application security vulnerabilities with the goal of having it take somewhere around 1-3 hours, depending on experience, to complete. Those who complete the game are rewarded with one of these awesome challenge coins:
Now, I know that there are people out there who look at one of these things and don’t even know where to start so, it is in the spirit of education and learning that I share with you my notes on how to complete the LASCON 2017 Badge Game.
Stage 1
On the back of the LASCON badge it reads as follows:
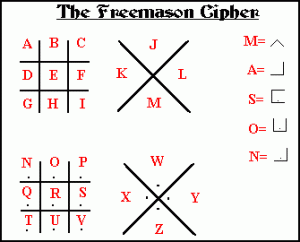
Another year, another gameSolve the puzzles, write your nameThese characters aren’t a work of artAsk a mason how to start
To start the badge game go to nocsal dot lascon dot org
|
<?php
|
|
|
// Test ability to grab winners table from the database
|
|
|
$servername = “localhost”;
|
|
|
$username = “lascon”;
|
|
|
$password = “e3fmGYHDrc6MNCEMmLWj”;
|
|
|
$dbname = “lascon”;
|
|
|
$conn = new mysqli($servername, $username, $password, $dbname);
|
|
|
$sql = “SELECT * FROM lascon_winners”;
|
|
|
$result = $conn->query($sql);
|
|
|
$array = $result->fetch_array();
|
|
|
print_r($array);
|
|
|
$conn->close();
|
|
|
?>
|
Stage 3
Even though the database connection that we found uses a servername of “localhost”, it turns out that mysql is open on the public IP interface of the server as well. We can use a mysql client to connect to nocsal.lascon.org with username “lascon” and password “e3fmGYHDrc6MNCEMmLWj” (mysql -h nocsal.lascon.org -u lascon -p). Once in the database, the user has access to read the lascon database and will see a “lascon_winners”, “users”, and “websites” table. When you try to insert into the lascon_winners table, you quickly realize that you do not have insert permissions, so you cannot insert into the lascon_winners table. In the users table, you see an entry with username “admin” and password “NFJXaTNuc0pyR2Y2c25iNG9Va1c=“. In the websites table, you see a bunch of sites and one hiding amongst the others is ttpcteebhz.lascon.org.
Stage 4
When you go to http://ttpcteebhz.lascon.org in your browser, you see a form with a spot for a username and password. You can base64 decode the string you found int he database (NFJXaTNuc0pyR2Y2c25iNG9Va1c=) to get the value “4RWi3nsJrGf6snb4oUkW”. Once you have that, you can log in with username “admin” and password “4RWi3nsJrGf6snb4oUkW”.
Stage 5
Once logged in with the username and password, you see a blank page. Once you view the page source, however, you see that it contains a hidden form and fields:
The last part of the challenge you could accomplish with a proxy tool, but I just used the Developer Tools in Chrome. I changed the hidden fields to text fields, removed the readonly values, and then added a form submit button. Once submitted, the game is over and you win!
A Quick Summary of Puzzles Solved / Vulnerabilities in the Badge Game
- Freemason Cipher
- Directory Traversal
- Information Disclosure in Comments
- Directory Browsing Enabled
- Hard-Coded Database Credentials
- MySQL Service Publicly Accessible
- BASE64 Encoded Passwords
- Hidden and Read-Only Form Fields
- Missing Form Submit Button



November 2nd, 2017 at 9:38 am
get your bullshit conspiracy freemasonry christianity mythology shit out of the hacker world
November 2nd, 2017 at 12:20 pm
I approved your comment because I want others to see just how insane it is. You don’t know me from anyone so for you to assume that I “don’t like atheism” is nuts. The LASCON Badge Game isn’t about religion in any way. It used a Pigpen (aka Freemason) Cipher as a means to get from the badge to the website. It’s a puzzle to solve, not a statement on religion. If you’re not smart enough to realize that ciphers ==> cryptography and what that has to do with Information Security, then you probably don’t belong in the “hacker world”. Just because you can use Tor Browser to view a website doesn’t make you a hacker. 😉