Are Invisible Barbarians At Your Gates?
A couple of weeks back, HD Moore posted a blog entry entitled
“Security Flaws in Universal Plug and Play: Unplug, Don’t Play” supporting a Rapid7 Whitepaper in which he discusses the 81 million unique IP addresses that respond to UPnP discovery requests on the Internet and the 23 million fingerprints that match a version of libupnp that exposes the systems to remote code execution. His research on the subject is fascinating and I highly recommend reading it over, but that’s not the reason why I’m writing this. The first question this research had me asking myself is whether or not my organization utilizes UPnP for anything. As far as I can tell, the answer to this question is, thankfully, no. Next, out of curiosity I began to wonder how many people were out there actively trying to find these exploits. A perfect opportunity to fire up our new LYNXeon tool.
Our LYNXeon tool is configured to consume NetFlow data provided by literally hundreds of routers and switches in our global environment. One of the most interesting things about it is that it can be used to see the traffic that comes in from our edge routers before it gets squashed by our firewall. Utilizing this tool in this way, we can visualize the so-called “Barbarians” at our gates. These are the hackers that are out there trying to find the weak spots in our security in order to get in. And since I know that UPnP is not a service that we offer up to the Internet at large, it makes finding the guys who are looking to exploit it that much easier.
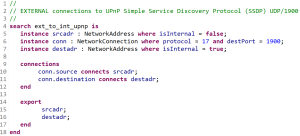
I fire up LYNXeon and my first step is to generate what is known as “PQL” or “Pattern Query Language”. While their Cyber Analytics Catalog offers up a ton of templates to use to find potential threats, PQL is the base of all those queries and writing your own allows you to define your own catalog of things to look for. The language is pretty easy to understand. First you define the characteristics of the connections that you are looking to find. After doing some research, I found out that HD was looking for openings on UPnP’s Simple Service Discovery Protocol (SSDP) service which typically runs on UDP/1900. So, my query is for connections from external source IPs to internal source IPs using the UDP protocol on port 1900. Once the connections have been defined, all that is left to do is define the data that you want to see in the results. In total, my PQL code is 15 lines of code:
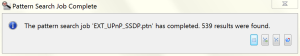
Now it’s officially time to make these invisible Barbarians visible. I tell LYNXeon to only show me results over the last day (to reduce the amount of time the search takes) and then tell it to “Execute Pattern Search” using the pattern file that I just created. Searches will vary in time based upon the timeframe searched, the number of forwarding devices, and how complicated your search criteria are. For me, this search returned 539 results in one minute and 38 seconds.
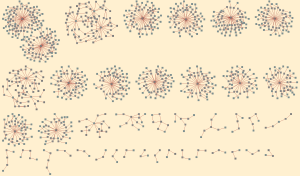
Now that I have results, I just need to select how to view them. My personal favorite is viewing the results in the Link Explorer. This will show my data as nodes on a pictoral graph. I make one quick adjustment using a organizational feature called “Force Directed Layout” to make the pictures look pretty and voila!
OK, so zoomed out it looks like a bunch of spider webs. Now the fun begins as we begin zooming in on each cluster to see what is going on.
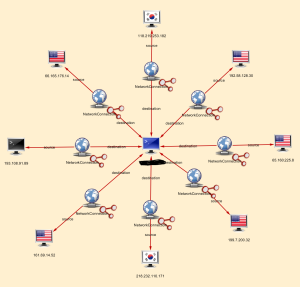
I’ve blacked out the IP address of the system these guys are connecting to as it is irrelevant for the purposes of this post, but you can clearly see that in the past day this one system has had eight unique IP addresses attempt to connect to it on UDP port 1900. I’ve got dozens more just like these on that big graph above with varying degrees of complexity. From here, LYNXeon allows me to resolve DNS and/or ARIN names for the associated IP addresses. I can also expand upon those sources to see what else of mine they’ve been talking to. Is that cool or what? It’s taken me minutes to find these potential threats and with little more than a few clicks of the mouse. The Barbarians are most definitely at my gates silently pounding away and chances are pretty good that they are doing the same to you. The question is….can you find them?

Leave a Reply